Enterprise focused
Orca's product is enterprise focused and not designed for small companies. Nevertheless, Zettasecure can offer affordable prices even in a small scale.
Zettasecure and Orca Cloud Security help you to get an agentless cloud security solutions and compliance for AWS, Azure, GCP and Kubernetes. Find vulnerabilities, malware, configuration issues, lateral movement risks and other threats in a timely manner. More to be come! The platform includes features such as vulnerability management, multi-cloud compliance, cloud workload protection, and AI-driven security. Recognized with awards like Forbes Cloud 100 and GigaOm Radar for CSPM, Orca Security is the 2022 AWS Security Partner of the Year.
Enterprise focused
Orca's product is enterprise focused and not designed for small companies. Nevertheless, Zettasecure can offer affordable prices even in a small scale.
Deployed within Minutes
By utilizing present data from the shared storage and the metadata of your cloud instances, the Orca security solution is agentless and still achieves complete visibility without sending a single packet over the network or running a single line of code in your environment - Just simple!
Context aware Security
Move away from guesswork, alert fatigue and false positives. With context aware security Orca's solution will effectively prioritizes risks and threats across your clouds. No matter if GCP, Azure or AWS - Orca got you covered!
Vulnerability Management
Orca leverages 20+ vulnerability data sources to discover and prioritize vulnerabilities across your entire cloud estate within minutes of deployment.
Lateral Movement Risk
Orca detects risks and vulnerabilities that could enable lateral movement in your cloud estate and recommends remediation steps to strengthen your security posture.
Malware Detection
Orca agentless SideScanning™ performs signature-based and heuristic malware scanning with no impact on cloud workloads to effectively detect and prioritize malware on AWS, Azure, and GCP.
Misconfiguration
Within minutes, Orca detects and prioritizes misconfigurations across your entire cloud estate, leveraging key compliance frameworks to help guarding your environment against breaches.
Sensitive Data Detection
Verify the security of your most important data. Orca scans your entire cloud estate to discover sensitive data that is not properly protected or has been compromised and prioritizes identified risks based on environmental context.
Identity and Access Management
Orca detects, prioritizes, and continuously monitors for common and obscure identity and access management (IAM) misconfigurations across your public cloud estate to meet stringent IAM compliance mandates and to improve your cloud security posture.
Orca Security, the cloud security innovation leader, provides instant-on security and compliance for AWS, Azure and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents or sidecars.

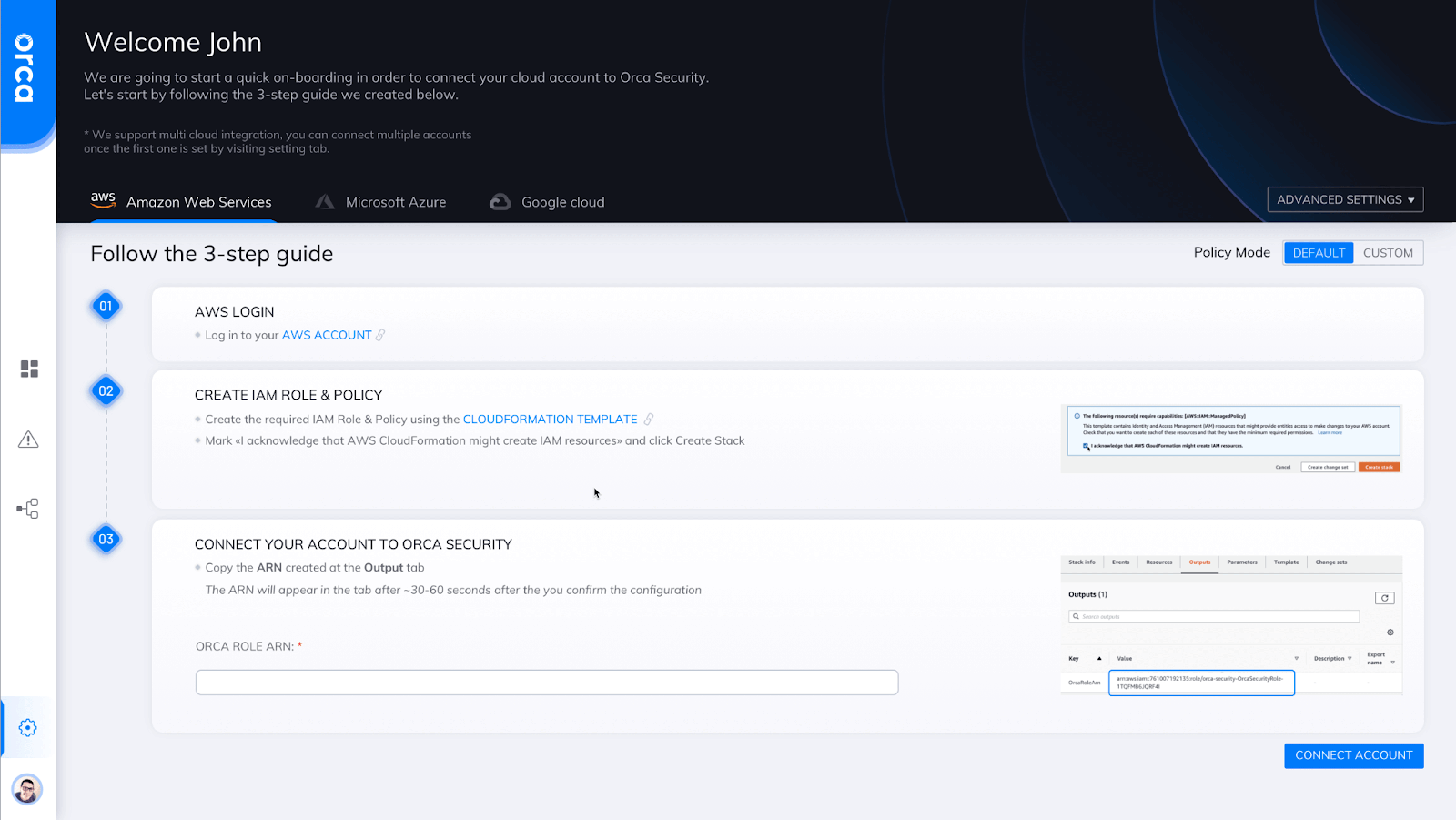
Orca Cloud Security deploys in minutes. Users need to login to their cloud account, then provision Orca with read-only access and hit start. That's it - Easy as one, two, three!
|
|
Business |
Premium |
|
Cloud Security Posture Management |
||
|
Cloud Asset Inventory |
||
|
Permissions and Privileges Management (CIEM) |
||
|
Vulnerability Management |
||
|
Lateral Movement Risk Detection |
||
|
Kubernetes Control Plane Assessment |
||
|
File Integrity Monitoring |
||
|
Malware Scanning |
||
|
Workload CIS Benchmarks |
||
|
Container Registry Scanning |
||
|
Virtual Machine Image Scanning |
||
|
Compliance Frameworks |
100+ |
100+ |
|
Custom Compliance Frameworks |
||
|
Alert prioritization |
||
|
Attack Path Analysis |
||
|
Custom Dashboards |
||
|
From the News widget |
||
|
Auto remediation |
||
|
Custom alert creation |
||
|
Alert automations |
||
|
Instance Scanning |
Sampling (Group rep) |
All Members |
|
Scheduled Scanning |
Daily |
Daily |
|
Manual Scan Invocation |
||
|
Shift Left capabilities |
||
|
Cloud Detection and Response |
||
|
DSPM - PII detection on Managed and Unmanaged Databases |
||
|
DSPM - PII Detection on Storage Buckets |
||
|
API security - External Exposure, Inventory, and Compliance |
||
|
Agent Protection |
||
|
SaaS Deployment |
||
|
In Account Deployment |
||
|
Role-Based Access Control |
||
|
Single Sign-On |
||
|
Business Unit support |
||
|
Integrations(Jira, ServiceNow, Slack, and others) |
||
|
API Access |
||
|
Reporting |
||
|
Scheduled reports |
||
|
Early Access to Beta Features |
Zettasecure has mostly everything to get you covered. If you have special requirements or other inquiries just sent us a mail or contact us with the button below.
Get in touchOrca's price is determined by the concept of workloads, which serves as its billing unit. The average number of workloads scanned is a key factor influencing the overall cost. The calculation of workloads is based on various assets in your environment, including VMs, container hosts, serverless functions, and other relevant components. Container images and VM images are considered billable workloads, but their inclusion in the workload calculation depends on whether they are enabled in your configuration.
Billing with Orca is based on the daily scanning of workloads and the cost is determined by calculating the rolling average over the billing period. This approach provides a flexible and dynamic billing structure that aligns with the evolving nature of the scanned workloads. If you got all the numbers right it is multiplied with the list price which is ranging from 450$ to 210$ per Workload. This is not a fixed price and can move up or down depending on the consumed amount.
Orca is an agentless cloud security platform that can assess cloud and workload metadata to evaluate risks within an organization. Even without agents, Orca can determine the risk posture of container workloads in cloud Kubernetes clusters or container hosts. The innovative approach that Orca uses to scan workloads is called SideScanning™ and utilizes cloud provider snapshot mechanisms. With SideScanning, Orca can perform a deep inspection on nodes that host containerized workloads and peer into the containers which execute on these hosts.
Orca’s comprehensive coverage includes malware scanning on cloud assets. Orca utilizes a leading third-party engine to scan for malware which includes executables, scripts, zip files, and other file types. Orca’s Malware Scanner uses signatures and heuristics to identify malicious files. Malware that is present can indicate an active or prior breach, many customers have discovered cases where their current solution for anti-malware is either not installed on systems in the cloud or have simply failed to detect them.
We are happy to help you with every problem you are encountering and will give you the right contact if something is not working as expected. Zettasecure is here for you to support your company with the help you deserve.
The Orca Cloud Security Platform uses a multi-tenant architecture that is logically segmented and restricts customer information. This architecture brings many benefits, like allowing us to satisfy the needs of multiple tenants (customers) using the hardware resources and staff needed to manage just a single software instance. By using a multi-tenant service our customers operate in virtual isolation from one another. However, organizations can configure and use the Orca Cloud Security Platform as though they each have a separate instance. With logical segmentation, an organization's data and customizations remain secure and insulated from the activity of all other tenants. Because Orca's Cloud Security Platform is a cloud service, you never have to update your software or worry about your hardware. This also allows Orca to make frequent, automatic, and seamless improvements to our service that benefit our entire customer base. All of this is possible because of multi-tenancy. The data within this multi-tenant architecture is stored at rest using AES-GCM 256 bit encryption and in transit using TLS 1.2.
Simply because we are offering better prices by an increasing service level - A more personal help will always win against a hotline. Additionally we are compensating your impact on our earth by using this service. So it's a win for everyone - The environment, you, our partner and us!
Sure! Please contact us and we can offer you a Proof-of-Concept for your Cloud infrastructure. We will implement it together and assess for vulnerabilities. All that for free! (Interesting to find Log4J vulnerabilities - Isn't it?)